Unmasking Secret Blizzard: The Russia-Linked APT Group Utilizing Others’ Infrastructure
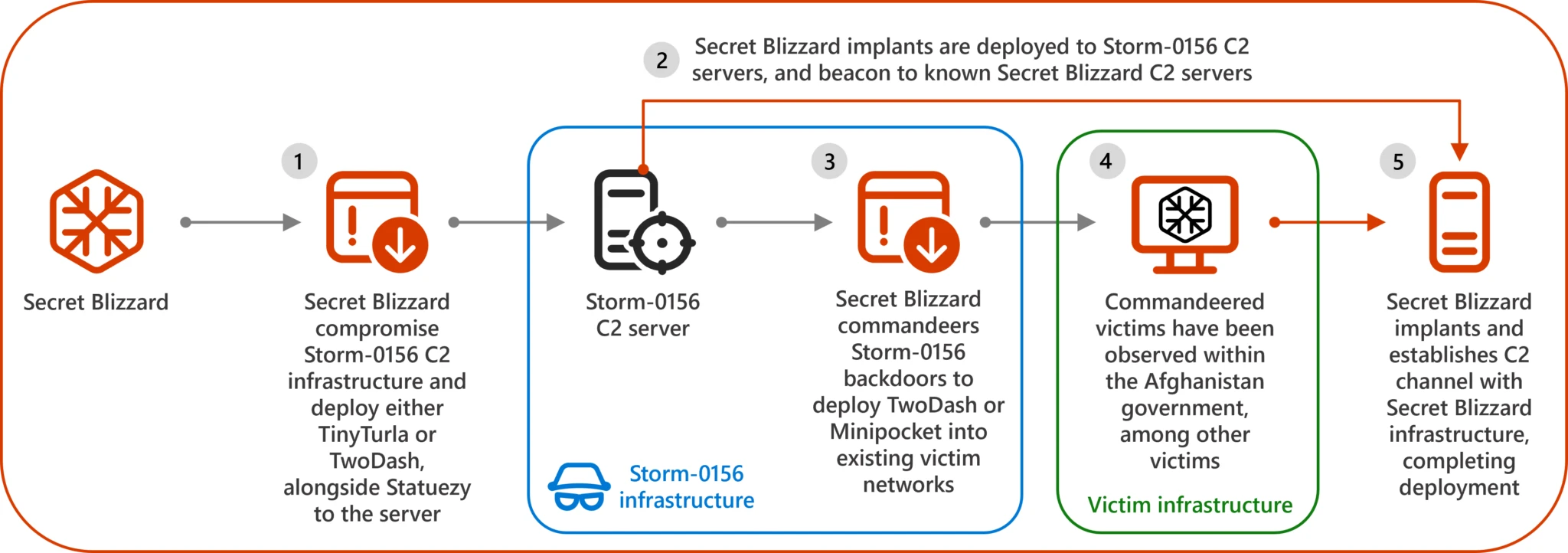
In the ever-evolving landscape of cybersecurity threats, one group has caught the attention of researchers and organizations alike: the Russia-linked Advanced Persistent Threat (APT) group known as Secret Blizzard. Over the past seven years, this elusive group has been observed leveraging the tools and infrastructure of at least six other threat actors, showcasing a level of sophistication and adaptability that raises alarms within the cybersecurity community. Microsoft Threat Intelligence has gathered compelling evidence highlighting this concerning trend.
Secret Blizzard, also referred to in some circles as Tu, has managed to integrate various tactics and tools from competing APT groups, making it a formidable player in the world of cyber threats. The implications of this behavior are significant, as it not only complicates attribution efforts but also highlights the collaborative nature of cybercrime, where groups can share resources and techniques to enhance their capabilities.
Interestingly, this isn’t the first time we’ve seen APT groups collaborate. For instance, the China-linked APT group Salt Typhoon has recently made headlines for breaching telecommunications companies across dozens of countries, demonstrating that sophisticated cyber threats are not limited to one region or ideology.
As researchers continue to investigate the intricate web of relationships among these APTs, it becomes increasingly vital for organizations to bolster their cybersecurity measures. Understanding the tactics, techniques, and procedures (TTPs) employed by groups like Secret Blizzard can aid in developing more robust defenses against potential breaches.
In conclusion, as the landscape of cyber threats continues to evolve, staying informed about groups like Secret Blizzard is crucial for businesses and individuals alike. By understanding the methods of these APTs, we can better prepare for the challenges ahead. For more insights on cybersecurity and threat intelligence, be sure to explore our other articles on related topics.