Introduction
In a startling revelation, cybersecurity researchers have uncovered malicious packages on npm and PyPI targeted at Solana users, exploiting vulnerabilities to pilfer private keys and drain funds from digital wallets. This growing threat calls for heightened vigilance in the ever-evolving landscape of online security.
Exploiting the Popularity of Solana
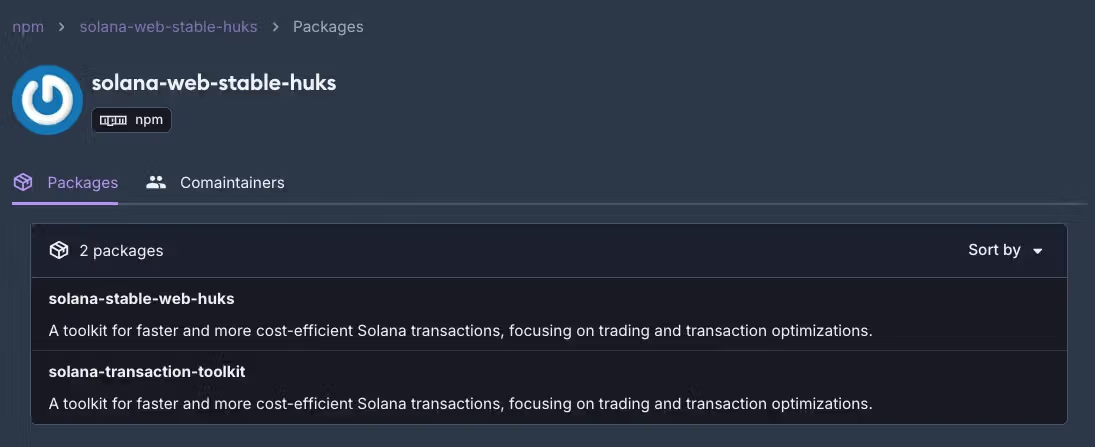
Researchers from Socket have identified various malicious packages mimicking popular libraries within the npm and Python Package Index (PyPI) repositories. These packages, camouflaged as tools for Solana cryptocurrency transactions, are engineered to stealthily exfiltrate private keys through email services like Gmail. By utilizing typosquatting strategies on well-known libraries, such as @async-mutex/mutex and dexscreener, the threat actors have orchestrated a methodical approach to compromise users’ wallets.
Technical Intricacies of the Attack
The malevolent packages, primarily identified as solana-transaction-toolkit and solana-stable-web-huks, not only steal sensitive information but also programmatically siphon off funds from compromised wallets, transferring up to 98% of the assets to addresses controlled by the attackers. This insidious tactic allows cybercriminals to maintain a low profile by leaving a small percentage of the original balance untouched to avoid drawing user suspicion. Notably, these transactions are facilitated without raising alarms, as they exploit Gmail’s SMTP servers to facilitate the stealthy exfiltration of private keys.
Persistence of Threats and Calls for Action
Despite alerts from experts requesting the removal of these packages, many remain active within npm. Additionally, Socket discovered GitHub repositories masquerading as genuine Solana resources, further amplifying the potential for widespread damage. Developers and users engaged in the Solana ecosystem face significant risks as these malicious tools proliferate, emphasizing the necessity for stringent security measures.
Protective Measures and Best Practices
To combat such threats, cybersecurity professionals recommend a series of protective steps, including rigorous verification of package authenticity, monitoring of download counts, and a keen awareness of publisher history. Regular audits of code dependencies are essential to prevent the introduction of potentially harmful packages. Furthermore, maintaining strict access controls around private keys and using isolated environments for testing scripts are vital strategies for safeguarding sensitive information.
Key Takeaways
- Malicious npm and PyPI packages target Solana wallets, stealing private keys and draining funds.
- Threat actors utilize clever tactics, such as typosquatting and Gmail exfiltration, to remain undetected.
- Ongoing vigilance is necessary; active packages still exist despite expert warnings.
- Implementing security best practices can mitigate risks associated with package vulnerabilities.